Active Directory password synchronization. This feature applies the Windows passwords of users registered in an Active Directory domain to their Domino HTTP and/or Notes ID passwords. Use this information to configure your network, users, servers (including Web servers), directory services, security, messaging, widgets and live. Enabling the Active Directory Connector on your account. The first thing you need to do is to enable the Active Directory Connector on your account. This is done from the Password Boss Portal. Login to the portal as an admin user and go to Connectors. Click Install to start the install process. Copy the authentication token.
- Active Directory Password Requirement
- 1password Active Directory Interface
- 1password Saml
- 1password Active Directory
Password reset tickets: the bane of both IT teams and end users. When the number of password reset tickets increases, IT teams often push more critical issues down the queue, so that users don't have to put their work on hold for too long while their passwords are reset. When left unchecked, password reset tickets can become expensive; since close to 30 percent of all help desk tickets are caused by forgotten passwords, it's unsurprising that several large businesses have spent over $1 million trying to resolve password-related help desk calls.
ADSelfService Plus offers self-service password management as a solution for password reset tickets. Simply put, whether it's a forgotten Office 365 or Active Directory (AD) password, ADSelfService Plus enables users to reset their passwords on their own, without IT assistance.
Self-service password reset from anywhere, at any time
With the adoption of cloud applications and bring your own device (BYOD) policies increasing, users are leveraging multiple access points aside from their Windows PC to complete their work. ADSelfService Plus enables users to perform self-service password reset and account unlock, regardless of whether they're in the office, on the move, or at home.
Password reset from logon screens.
Password reset from mobile devices.
Password reset from a private network.

Password reset from web browsers.
Supported platforms
ADSelfService Plus supports multiple user directories including AD, OpenLDAP, AD LDS, G Suite, MS SQL, Salesforce, Office 365, AS400, HP UX, Oracle DB, and more.
Stringent multi-factor authentication techniques (MFA) to secure password resets
ADSelfService Plus enables admins to trigger a preconfigured authentication workflow once users initiates a password reset process. It offers over 14 authentication techniques including biometrics and YubiKey to authenticate users during self-service password reset and account unlock. Some users have access to sensitive business data, and if their account is cracked by a malicious hacker, it can lead to disastrous consequences. To combat this, ADSelfService Plus offers admins the option to enforce different authentication types for different types of users.
A complete list of authenticators supported by ADSelfService Plus

How to reset forgotten Windows passwords using ADSelfService Plus
Types of password reset tickets admins and help desk teams encounter from end users
- I have forgotten my Windows login password.
- I am not able to log in to my account.
- Someone has changed my Windows XP password, and I want to reset it.
- I am not able to log in to my account with my domain password.
- How do I recover my account? How do I change my user password?
- I have shared my password identity with my fellow employee and want to change it to a new password. How do I change my password in AD?
- Can I use my neighbor's machine and change my domain password using a web browser?
- Can I change my password from the Ctrl+Alt+Del screen?
These routine password queries can be eliminated using a self-service password reset tool like ADSelfService Plus.
Ensure 100 percent enrollment with ADSelfService Plus
Before users can take advantage of the password reset tool, they must complete enrollment. Users need to enter their mobile phone number and email address, answer security questions, or provide other details in ADSelfService Plus to register for self-service employee password management. Learn more about enrollment.
ADSelfService Plus enables IT admins to:
Send alerts
Force users to enroll
Preload user profiles
Upload enrollment data
Other key features of ADSelfService Plus
1. Self-Service Account Unlock
Allow users to unlock accounts and reset passwords for their cloud accounts, including Office 365, G Suite, Salesforce, and Zendesk in addition to their AD account. Learn about self-service account unlock.
2. Password Synchronizer
Organizations can effectively deal with password fatigue by syncing user domain passwords across enterprise applications like Office 365, G Suite, and Oracle. For password changes through the Ctrl+Alt+Del screen or resets via the ADUC console, the new password is synchronized across connected applications using a password sync agent. Learn about the password sync agent.
3. Password Expiry Notifier
Remind users of their upcoming AD password or account expiration date via email, SMS, or push notifications. Send multiple notifications at regular intervals so alerts don’t go unnoticed, ensuring users change their passwords before they expire. Learn about password expiration notifier.
4. Password Policy Enforcer
Admins can create multiple custom password policies using advanced password policy options to ban weak passwords, palindromes, etc. based on users’ privileges, and enforce these policies based on organizational units (OUs) and groups. Learn about custom password policies.
5. Password reset notification
Once users complete the self-service password reset process, ADSelfService Plus triggers an SMS, email, or push notification as a security measure. Learn about password reset notification.
6. Comprehensive reports
ADSelfService Plus helps admins by providing detailed reports like the Password Reset Notification report, Identity Verification Failure report, the Weak Password Users report, and more. Learn more about reports.
Benefits of ADSelfService Plus
- Improves ROI: Eliminates the major source of help desk calls. Calculate your ROI here.
- Improves IT security: Ensures users create strong passwords and secures endpoint logons.
- Improves user experience: Helps users reset passwords from anywhere, at any time.
- Helps with compliance: ADSelfService Plus helps comply with NIST, FFIEC, PCI DSS, CJIS, Section 508, and HIPPA regulations.
Self-service password reset tool for Windows AD, G Suite, etc.
Thanks!
Your download is in progress and it will be completed in just a few seconds!
If you face any issues, download manually here
Password self-service
Free Active Directory users from attending lengthy help desk calls by allowing them to self-service their password resets/ account unlock tasks. Hassle-free password change for Active Directory users with ADSelfService Plus ‘Change Password’ console.
One identity with Single sign-on
Get seamless one-click access to 100+ cloud applications. With enterprise single sign-on, users can access all their cloud applications with their Active Directory credentials. Thanks to ADSelfService Plus!
Password/Account Expiry Notification
Intimate Active Directory users of their impending password/account expiry by mailing them these password/account expiry notifications.
Password Synchronizer
Synchronize Windows Active Directory user password/account changes across multiple systems, automatically, including Office 365, G Suite, IBM iSeries and more.
Password Policy Enforcer
Ensure strong user passwords that resist various hacking threats with ADSelfService Plus by enforcing Active Directory users to adhere to compliant passwords via displaying password complexity requirements.
Directory Self-Update & Corporate Search
Portal that lets Active Directory users update their latest information and a quick search facility to scout for information about peers by using search keys, like contact number, of the personality being searched.
Tracking and auditing changes to passwords in an Active Directory (AD) domain are crucial to maintaining a secure environment and heading off bad actors early. Thankfully, AD offers the information necessary to track these changes, despite being difficult to parse and understand at times. LAPS is a great example of this.
In this article, you’re going to learn how to enable Active Directory auditing of passwords, how to filter events in the Event Viewer and use PowerShell to more easily audit the results with a script.
This tutorial is sponsored by SpecOps and their useful tool Password Auditor.
Prerequisites
If you’d like to follow along with this tutorial, please be sure you have the following:
- An Active Directory environment with at least one domain-joined workstation. The tutorial is at a domain functional level of Windows Server 2016, however, Advanced Audit Policies were introduced in Windows Server 2008 via a logon script and via a GPO in Windows Server 2008 R2.
- Remote Server Administration Tools (RSAT) for Active Directory installed on your domain-joined workstation
Enable Group Policy for Active Directory Auditing
The necessary auditing information you need to audit AD password changes is stored on domain controllers (DC), but the domain controller in the Primary Domain Controller (PDC) emulator role will ultimately process the request. But, by default, the necessary auditing isn’t enabled on DCs. Let’s change that.
To find the DC holding the PDCe role, use the PowerShell command, (Get-ADDomain).PDCEmulator.
To enable password change auditing, create a new group policy object (GPO). This GPO will be created and linked to the entire domain.
You could change the Default Domain Policy but Microsoft recommends against this. If you ever need to make a change across DCs in your environment, always create a separate GPO.
Though you are creating and linking a GPO to the entire domain, the relevant audit events are only available on DCs. But, it is beneficial to have those same logs on domain-joined clients because it may be useful in the event that a local non-AD account password is changed. If you’re only auditing Active Directory accounts, you can instead link the GPO to the Domain Controllers organizational unit (OU).
On your domain-joined workstation, create a GPO that forces DCs to begin auditing password changes:
- Open the Group Policy Management snap-in by going to Start → Run and typing gpmc.msc.
2. Click on Create a GPO in this domain, and Link it here… and give the policy a name. This tutorial’s example will use the name Active Directory Password Auditing.
3. Once the policy has been created, right-click it, and choose Edit to open the Group Policy Management Editor.
4. Navigate to Computer Configuration → Policies → Windows Settings → Security Settings → Local Policies → Audit Policy → Audit account management.
5. Next, double-click on the Audit Account Management policy setting and check the checkbox Define these policy settings while ensuring both the Success and Failure checkboxes are checked. By doing so, successful and unsuccessful password attempts will be logged.
6. Click OK to close and exit the editor.
7. Open up a Remote Desktop (RDP) client and connect to the domain controller running the PDC emulator (PDCe) AD role.
All DCs process password changes but all DCs replicate password changes to the DC holding the PDC emulator (PDCe) role so technically, you only need to look at this DC’s events.
8. On the PDCe DC, open a command prompt or PowerShell console and run gpupdate to force a group policy update.
If you have PowerShell Remoting enabled on your DCs, you can also invoke a GPO update that way also.
Once the configuration changes have been made and group policy updated, you now have auditing events turned on and logging for account management. Read on to discover how to interpret these events.
Deciphering Account Management Event Logging
The category of audit events password changes fall under is called Account Management events. These events record information such as password change events and user account lockouts. Account Management audit events are logged as Windows events in the Security event log of a machine that has the auditing enabled.
On your domain-joined machine:
- Open up Windows Event Viewer by running eventvwr.msc or using the Start menu.
2. Right-click on Event Viewer (Local) and select Connect to Another Computer….
3. Provide the name of the DC running the PDCe role in the Another computer: box and click OK to connect Event Viewer to the DC’s event source.
4. Expand the Windows Logs item and click on Security. This will bring you to the Security log as shown below.
Inside of the security log, you’ll find various events with a source of Microsoft Windows security auditing and User Account Management task categories as shown in the filtered view below.
Each Windows event has a unique ID that represents the type of event. Though there are several event IDs that the Microsoft Windows security auditing source contains, the primary event IDs that you should be interested in for password changes (and user lockouts) are:
- 4723 – An attempt was made to change an account’s password.
- 4724 – An attempt was made to reset an account password.
- 4740 – A user account was locked out.
- 4767 – A user account was unlocked.
You’ll see a lot of events in the Security log so you’ll need to create an apply some filters to narrow down only password changes.
Filtering on Password Change Events
Within the Event Viewer, you can create a filter. A filter is a way to limit the number of events that show up and is mandatory when combing through the Windows Security event log.
To create this filter in the Event Viewer:
- Right-click on the Security log and click on Filter Current Log… as shown below.
2. In the Filter Current Log dialog box, create a filter to only find password change events using the following criteria and click on OK.
- Event Sources:Microsoft Windows security auditing.
- Event IDs: 4723,4724,4740,4767
- Task Category: User Account Management.
When you’re complete, your Filter Current Log screen should look like below.
By filtering the Event Viewer, on the domain controller, to just the important event IDs a targeted list of events that have occurred specific to password and password changes are shown below.
Voila! You now have all of the password change (and user lockout) events that have occurred in your domain since you’ve linked the GPO created earlier!
Find Audit Events with PowerShell
Even though you can use the Windows Event Viewer connected to the DC’s Security event log sometimes you need a faster approach. Perhaps you have some automation built in the background or would like to automatically monitor this event log. In this case, you should use PowerShell.
Using PowerShell allows you to perform the exact same function all within a single script. With a script, you won’t have to connect to DCs, create filters manually and manually parse through events.
To find important auditing events with PowerShell, use the Get-WinEventcmdlet. This cmdlet queries a local or remote event log and returns all events. It also has support for filters too just as the Event Viewer does. If you’ve already built a filter with Event Viewer, you can even, in fact, share that same filter with PowerShell!
Extracting the Event Viewer Filter
Since PowerShell can use the same filter as the Event Viewer, let’s save some time and extract that filter and use it with PowerShell’s Get-WinEvent cmdlet.
While still ensuring you’re still connected to the DC with Event Viewer:
- Go back to the Filter Current Log screen. You should still have all of the filter criteria set.
- Click on the XML tab at the top. This tab contains the raw XML that Event Viewer is passing to the event log to display only certain events. PowerShell also can use this XML.
- Select and copy all of the text been <Select Path=”Security”> and </Select> as shown below. This text is an XPath value that the
Get-WinEventcmdlet can use.
4. Open up a PowerShell console and paste in the following code snippet. You can see the FilterXPath parameter value is the exact same text extracted from the Event Viewer filter above.
When you run Get-WinEvent, you should see all of the same events you saw in the Event Viewer earlier as shown in the following screenshot.
You’ve now found all password change and user lockout events with PowerShell!
Buiding a Password Change Auditing Tool
You’ve seen how to use PowerShell’s Get-WinEvent cmdlet to audit AD events. If you plan to do this often, it’s always a good idea to use a reusable tool to use in other scripts or automation routines.
In this section, let’s build a PowerShell function called Get-ADPasswordEvent. This function will explore many techniques that can help you retrieve just the information that you want without all the additional properties that you get with Get-WinEvent.
To not bore you with all of the details, you can see a complete function already built for you below. This function performs a few different tasks:
- Creates the XPath filter
- Runs
Get-WinEventusing the filter retrieving the specific AD account management password events - Returns custom output relevant to the task at hand.
You can find more granular details in the code comments.
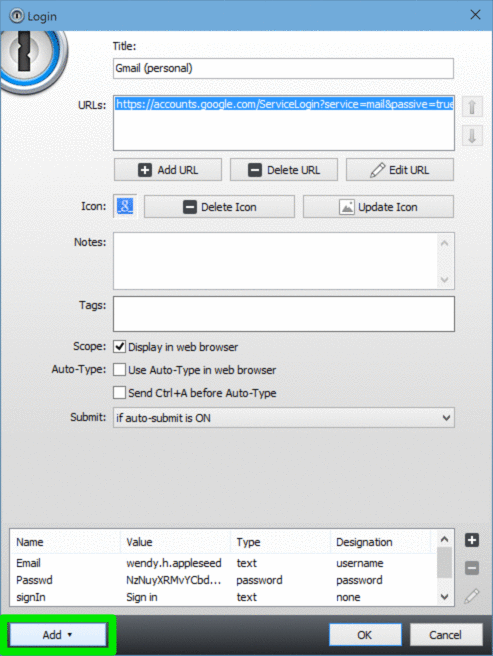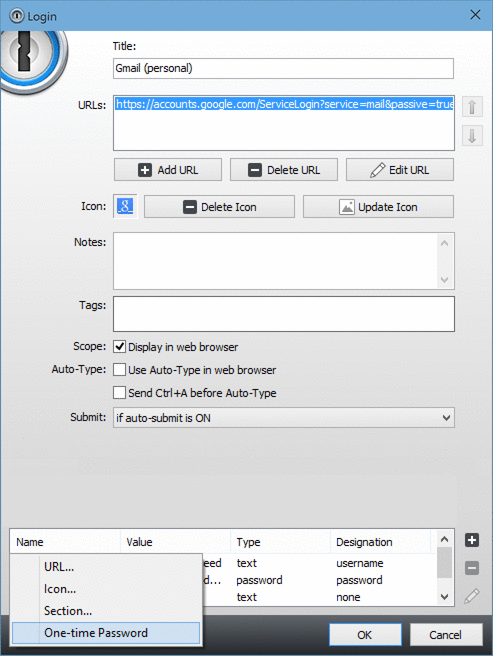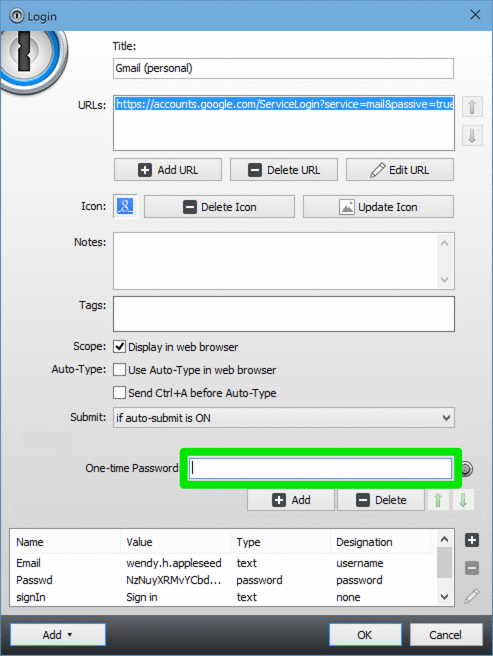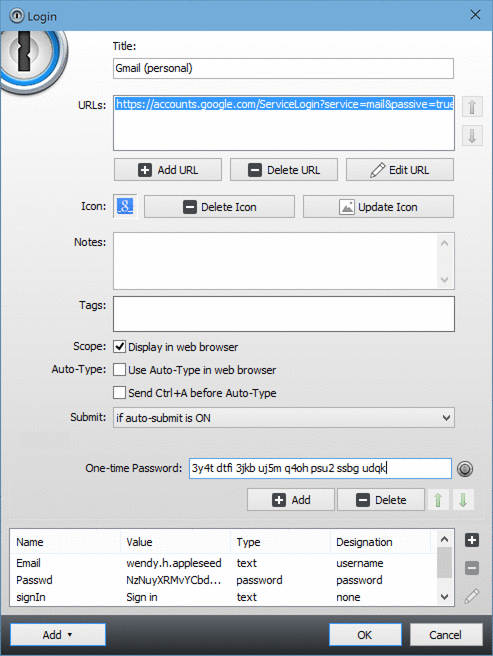
Active Directory Password Requirement
Once created, drop this function into a PowerShell console and run it with no parameters.
1password Active Directory Interface
Shown below is running Get-ADPasswordEvent. You can see that the function returns many success and failure events for password reset attempts.
You can pass the output of the Get-ADPasswordReset function to Format-Table to make the output a little easier to read.
1password Saml
Implementing Better Password Auditing Solutions
Whether you’re using the Event Viewer or PowerShell, you have to jump through a few different hoops to find AD auditing events. The native tools and abilities of Active Directory could certainly be expanded upon, and for that, third-party tools such as SpecOps Password Auditor can help.
1password Active Directory
SpecOps’ Password Auditor tool not only can find these events, but it can also create in-depth reports that include changes, expired passwords, blank passwords, and more. SpecOps Password Auditor can fill in the missing gaps for Active Directory password auditing.
Related
